GDPR Help: a summary of Europe’s new privacy laws and how they may affect your business
March 20, 2018
The following article is a guest post by Paul Bailey, Marketing & Design Director for Wesley Clover.
Recently Wales’ technology sector monthly networking event, Digital Tuesday, held an interesting event about Europe’s new GDPR (General Data Protection Regulation). This article dives into the questions and concerns that were raised at the event, and hopefully addresses people’s doubts in the answers given.
Common Questions:
Can I call someone from a business card?
Can I find someone’s email address online and contact them?
If I ring someone, will I be breaking the law?
Is CRM now dead because of GDPR?
There are some key aspects to this European wide ruling that we all need to be aware of. The ruling body in the UK that we will use for the sake of this piece is the ICO (Information Commissioner’s Office). They provide ample information about this subject on their website, but often start-ups will ignore this legislation and continue as they were without realising that they could be breaking the law. Plus, the information is so vast, finding where to start is the hard part!
GDPR is applied to EVERY citizen residing in or a legal resident of a country within Europe. Even a database with 99.9% North American data but 0.1% EU data needs to be treated the same as the new laws apply to those EU nationals. This is why the new GDPR rules matter to EVERYONE.
Where do I Start with my GDPR processes?
Cybersecurity is the foundation for good practice when it comes to GDPR. Holding peoples’ data is fine and as long as it is secure and there are policies in place to protect this data in the case of a breach. If you hold personal data in a CRM (Customer Relationship Manager), then you must ensure that the CRM itself is compliant.
Furthermore, your staff will need to be trained on how to handle personal data. What can they do with it? How can they handle it? When should they delete it (or securely shred it)? The onus is on the company to correctly train their employees to best understand how they can obtain and use peoples’ data.
Different jobs (whether in the same company or external), will have different company policies and processes. The onus, again, is on the company to provide suitable induction training into data protection and handling practices.
Fortunately, HutSix, one of the Wesley Clover Innovation Centre’s teams, is building an online tutorial that takes readers through the rules of GDPR. In particular, their course will allow you to answer questions, understand whether you and your colleagues are adhering to the regulations, and where you can improve. More on this tutorial from HutSix coming soon!
On the other hand, if you want a company to sure up your masses of data then File Facets can efficiently do this for you. File Facets provide the platform to enable you to comply with the legislation by acquiring your existing data from multiple sources, identifying personal information and flagging, moving, deleting or securing it.
The ICO wants to ensure that certain steps have been taken to limit exposure of personal data.You may still find yourself in a situation where your information is compromised, but if you have taken reasonable steps to prevent this from happening, then there is a greater chance that you won’t receive a huge fine. Or if you do, you could argue to have it reduced.
Should you receive a data breach, then the ICO will carry out an investigation. They will review the training history of everyone involved, the role they fulfil, whether it’s appropriate for them to have access to the data, and what they were able to do with it.
If you’re an individual looking at being recruited into the tech industry, now is a good time to make yourself as aware as you can with the data protection principles and thus give yourself a better chance at achieving your goal. Knowing how to handle someone’s data is extremely important. Even understanding some of the basic points outlined in this article will give you an advantage over other candidates.
One important tidbit is that the protection of data must be treated the same across all Locations, especially for servers or filing systems holding personal data outside of the EEA (European Economic Area) such as the United States or Canada. It is imperative that these countries must comply with GDPR when holding personal data of people within the EEA.
Six Principles of GDPR (plus one additional important one)
1. Lawfulness, Fairness and Transparency
The person whose data you hold must understand what you will do with their data. You need to stick to this promise and not change how it is processed (without their consent).
[article 5, clause 1(a)]
2. Purpose Limitations
Personal data can only be obtained and used where there is a legitimate and specified business interest. When contacting someone it must be under the promises originally obtained, or for new customers a legitimate interest must be identified prior.
[article 5, clause 1(b)].
3. Data Minimisation
Collected data must be adequate to fulfill the role intended but also limited to only what is necessary.
[article 5, clause 1(c)]
4. Accuracy
All data must be kept up to date and accurate. This limits possible identity theft or incorrect information contamination.
[article 5, clause 1(d)]
5. Storage limitations
Personal data should be kept in a way that allows identification in whole of a person and be kept for no longer than is necessary.
[article 5, clause 1(e)]
6. Integrity and confidentiality
Data Processors must handle data in an appropriate manner. They must ensure adequate security of the data including protection against accidental loss, inappropriate use or damage.
[article 5, clause 1(f)]
7. (Additional one) Accountability
This point isn’t in the original 6 principles but is very important: Accountability. You should be able to demonstrate that you and your team fully comply with the principles of data security. This means securing accurate documentation of policies and procedures, adequately training staff, and conducting risk assessments and audits to ensure that all possible areas are secured and understanding of how to control and handle personal data.
Data Processors or Data Controllers?
The processing of people’s personal data includes the act of using their data under permission. As a data processor, you have a legal requirement to only use what you need.
The data controller is the person who will determine how the data is processed. If you own a large database of customer details, then you are the controller, however, if you allow an external company to contact that data on your behalf then they are the data processors. If someone within your company is using your data, they are still classed as controllers.
For instance, Enjovia, a gift voucher management tool handles personal details passed to them from hotels such as The Celtic Manor Resort. The Celtic Manor gathers the customer details and passes them through the interface to Enjovia, who then take payments on behalf of Celtic Manor and fulfill the vouchers using the processed name, address and credit cards etc. In this case, the Celtic Manor are the controllers of the data.
How do You Collect Your Digital Data?
The onus is on you as a company to train your staff how to obtain, collect and handle data. They need to fully understand your company’s policies and procedures. If there is a breach in your data, the ICO will ask what training your staff have received in order to identify if their training was sufficient. Everyone is legally obligated to share information about company breaches quickly via the ICO website.
Where Do You Store Your Digital Data?
You need to ensure that your data is secure online. Wesley Clover uses HubSpot because they are in compliance with GDPR regulations. However, they aren’t held responsible in the case of a breach because it was Wesley Clover’s choice as a company to use them as a data holding resource. In this case, Wesley Clover is still considered the controller of the information and held responsible in case of misuse.
Can I Keep Someone’s Data Forever?
You can’t keep personal data for longer than you need to. By this, we mean that if you have not contacted anyone within a couple of years, you should ask them if it is OK to keep their details on file, with the intention to send future newsletters or emails. They can then assure you of the opt-in (or out), allowing you the authorisation you need to keep their data on file. If your company isn’t using a person’s contact information for an extended length of time, however, you may want to consider whether you need to keep that data at all.
Stay Ahead of the Game – Privacy Policy
One thing that can easily be overlooked is your privacy policy. That small and almost hidden link at the bottom of the page next to your copyright notice.
The privacy policy needs to be obvious. Though it may remain fine in that corner of the website, you could consider adding it to your main menu to really keep the data police happy.
The privacy policy needs to be written in as simple terms as possible. It needs to be specific with how you’ll capture data, how you’ll store it, how you’ll use it, secure it, delete it etc.
A good example of a privacy policy is on Google, where it is written in clear sections and plain English. (Though that’s not a poke to copy it…promise).
To be Clear, What Information Does GDPR Apply to?
GDPR applies to personal data. How much personal data though? Again, if you can identify a person directly or indirectly from the data then it is considered personal.
If you have a first name only but also have that individual’s phone number, then that person can be found easily. If you have no names but an email address, then again, this person can be contacted, and potentially phished. In both these cases you would be liable should that data be compromised through a hack to your systems.
Don’t forget that business cards are sensitive data now under GDPR and they also need to be controlled.
Do I Really Need Permission to Contact Someone?
Here’s the key part; consent. The rules around consent mean that you must have a LEGITIMATE BUSINESS INTEREST in contacting that person. On the flip side, the person you’re contacting must also have a LEGITIMATE INTEREST in hearing what you have to say.
Contacting a Medical Centre to promote your online shopping is certainly irrelevant to that business and thus, there is no legitimate interest for either party. These types of contacts should never be approached. If you have that person’s details, then they need to be securely deleted.
A clean database is a happy database!
If someone hands you a business card, you therefore have a legitimate interest in speaking with each other. If your contact turns around and says they are not interested in your product, then you should follow up by asking if they can stay in your database for future business developments. If they are still un-interested, then you have to securely remove that persons’ details from your database.
Who Should I Care About the Most?
There are two people you need to keep happy. You should care about what your customers (or potential customers) would think about you contacting them, and also what the ICO would make of your contact.
If you’re located in Britain, you should treat the ICO as the supervising authority, and not do anything to upset them or breach the GDPR rules. Think about what the likelihood of the person you’re contacting complaining or even formally referring you to the ICO? It’s likely not worth the risk.
How Can I Quantify the Risk?
GDPR encourages you to develop ‘Privacy by Design’ and therefore you need to know where the risks are.
You need to build a GDPR Risk Register. To complete a risk register it might be easier to think about people rather than technology.
To do so, write down all the people in your company and then analyse the risk and interaction with each of those groups with regards to their handling of data. Then you can complete your audit for all of those risks and look into things like ‘the description of service’ (SIM cards, email list, supplier phone numbers), ‘What type of data is it’ (is it personal or sensitive data), ‘Valid reason to hold this data’ (business contact, legal requirement), ‘Where is it stored’ (server in Hubspot, folder in a department) and finally the ‘Risks’ (printing out of data, incorrect contact, lost passwords).
Once you complete this GDPR Risk Register and Audit, then you can accurately see the holes in your data security.
As I said at the beginning, data and cybersecurity are the very foundation of GDPR rules.
I Found an Email on Someone’s Website, Can I Contact Them?
Even though that person hasn’t given you permission to contact them, Yes! That person has their details in the public domain and is on their website for contact reasons. Again, you should remember that you and the contact need legitimate interest before you contact them.
If they are not interested in what you’re offering after a conversation then you will need to remove their details UNLESS they have given permission to stay on your database and be contacted at a more suitable time. Consent given, box ticked.
The same rules apply to email contacts, postal marketing, as well as phone calls. Consent can be revoked after the first conversation in which case you should close the book, delete the data and move on.
I Bought an Email List, Can I Use it?
Again, going back to CONSENT, you need to know whether that database has permission to be contacted for your line of work and that the reason you are contacting them will be relevant. If the seller of the list has the consent, then the legitimate business interest concern is valid. If you cannot get the written consent then you should question the use or even purchase of that data.
I Sold a Product to a Person Several Years Ago, Can I Keep Their Details?
Under the goods and services agreement between you and that person or business, all the details required to fulfill that purchase will be obviously be kept by yourselves not only for business, tax and accountability reasons but for upselling and marketing in the future.
You can keep their details for legal business reasons, but their consent to be contacted after this purchase needs to be recorded. If you sold a car to a person several years ago then it would be relevant to contact them by email or phone about servicing, aftercare, product recalls etc. However, if you sold them a car last month then promoting a new car to them and better discounts in such a short time may not be the most business savvy decision.
Always be mindful of continuing to send information to your database. Nurture your database and treat it with love, rather than hitting it completely with as much information as possible. A higher churn and unsubscribe rate will probably occur with the latter!
I have a SaaS Product, What Concerns Do I Have?
A lot. As a service provider, you are storing on behalf of your clients their personal data and probably even their client’s personal data. Should you have access to this data? Maybe only in extreme situations and only after authorisation from the data controller.
Regardless of this, having GDPR rules as the platform for your handling of personal data is essential. Your platform needs to be 100% secured. In certain instances, some of your customers may want a slightly different approach to the handling of their data and therefore you need to think about flexibility to keep them happy.
Don’t forget it is their choice to use your platform, so they become the data controllers.
However, you need to be responsible with your security foundations to ensure the contract between you and your client is adhered to, and their data is controlled and respected.
To end, GDPR rules aren’t as scary as they initially seem. There is a massive common-sense approach to the handling of data. Cybersecurity and locking down your systems are at the heart and from there we can build.
Ensure the people in your organisation have access to the appropriate data and understad company policies and how to handle and use that data. The onus is on you as the company to train staff, so that everyone understands how to use and treat people’s personal data.
Complete a Risk Register and Data Audit to understand your potential risk in breaches of security – be that through cyber or physical abuse.
Consider your brand as the most important part:
Is it worth jeopardising to reach potential contacts? What is the likelihood of that person complaining or even involving the ICO? Have you added your data protection mandate to your websites policies and procedures document? Is this document in an easy place to view and access? Is it in plain English and able to be understood?
Before you contact someone, do you have a legitimate business interest in contacting them? Are you keeping data and not using it? If you no longer require the data, you must destroy it securely. Have you ensured that certain steps have been taken to train, secure and limit any exposure of your data?
Additional Resources
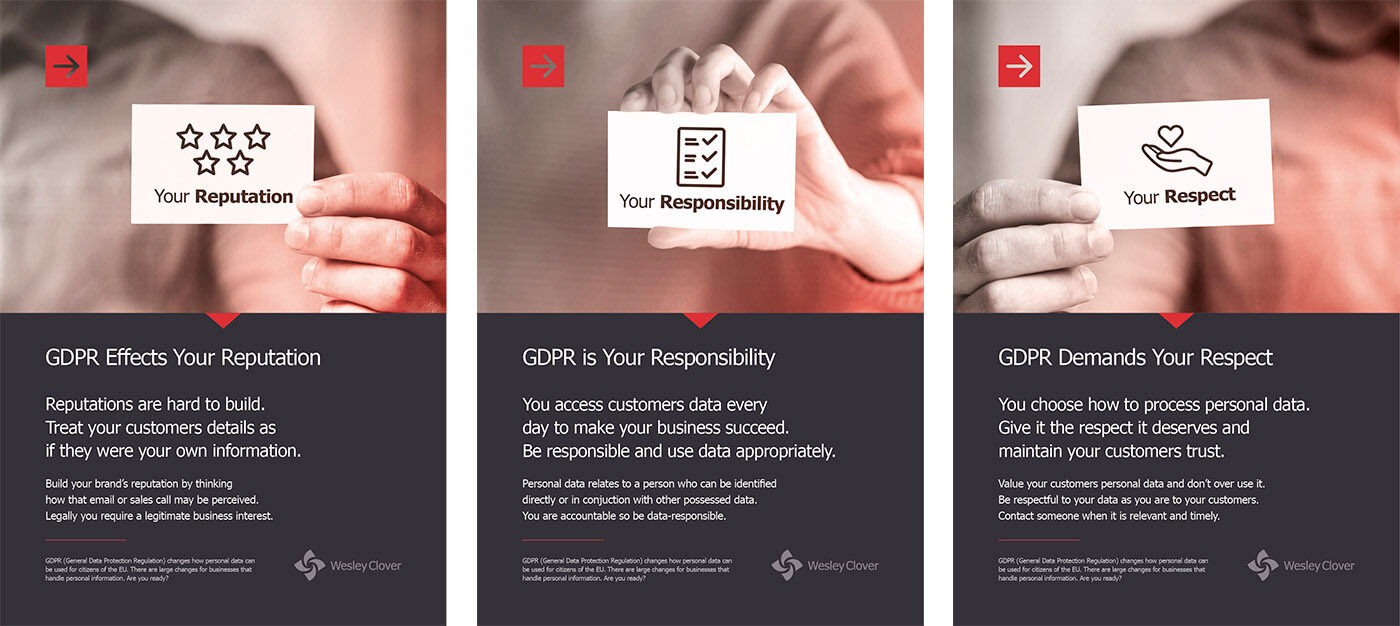
Download three posters made by Paul in high resolution PDF format by clicking here.
The ICO has a self-assessment online tool for your current levels of protection to ensure you are GDPR compliant as soon as possible. The results are eye-opening.
For an ICO guide on what steps you need to take now, please click and download the PDF from here.
More information on this Digital Tuesday event can be found here.
Disclaimer: This post is based off of Paul’s understanding of GDPR and EU data privacy. It is not legal advice but provides background information to help you better understand some important points.